Overview
Casdoor can be configured to support user login to the UI using identities from external identity providers that support SAML 2.0. In this configuration, Casdoor never stores any credentials for the users.
Now, Casdoor supports multiple SAML application providers. Icons of the providers will be displayed on the login page after being added to Casdoor. Here are the providers that Casdoor supports:
| Alibaba Cloud IDaaS | Keycloak | Custom |
|---|---|---|
| ✅ | ✅ | ✅ |
Terms
- Identity Provider (IDP) - The service that stores the identity database and provides identity and authentication services to Casdoor.
- Service Provider (SP) - The service that provides resources to the end user, in this case, the Casdoor deployment.
- Assertion Consumer Service (ACS) - The consumer of SAML assertions generated by the Identity Provider.
Configuration Values for Casdoor as SP
When configuring an external Identity Provider (such as Google Workspace, Azure AD, or other SAML IdPs), you'll typically need to provide the following values:
ACS URL (Assertion Consumer Service URL): This is the endpoint where the IdP will send SAML assertions. For Casdoor, use:
https://<your-casdoor-domain>/api/acs(replace<your-casdoor-domain>with your actual Casdoor domain, e.g.,https://door.example.com/api/acs)Entity ID (SP Entity ID): This uniquely identifies your Casdoor instance as a Service Provider. Use the same URL as the ACS URL:
https://<your-casdoor-domain>/api/acsRequest Method: The
/api/acsendpoint only accepts POST requests. Ensure your IdP is configured to send SAML responses via HTTP POST binding.
User Attribute Mapping
When a user authenticates through SAML, Casdoor extracts user information from the SAML assertion based on your provider's attribute mapping configuration. The username field is particularly important as it's required for user identification and creation in Casdoor.
If your IdP doesn't explicitly provide a username mapping or the username field comes back empty, Casdoor automatically applies a fallback strategy:
- First, it attempts to use the email address from the SAML assertion as the username
- If no email is available, it falls back to the NameID (unique identifier) from the assertion
This fallback mechanism ensures smooth authentication even when username attributes aren't explicitly configured in your IdP, which is common with providers like Azure AD where the default attribute claims might not include a separate username field.
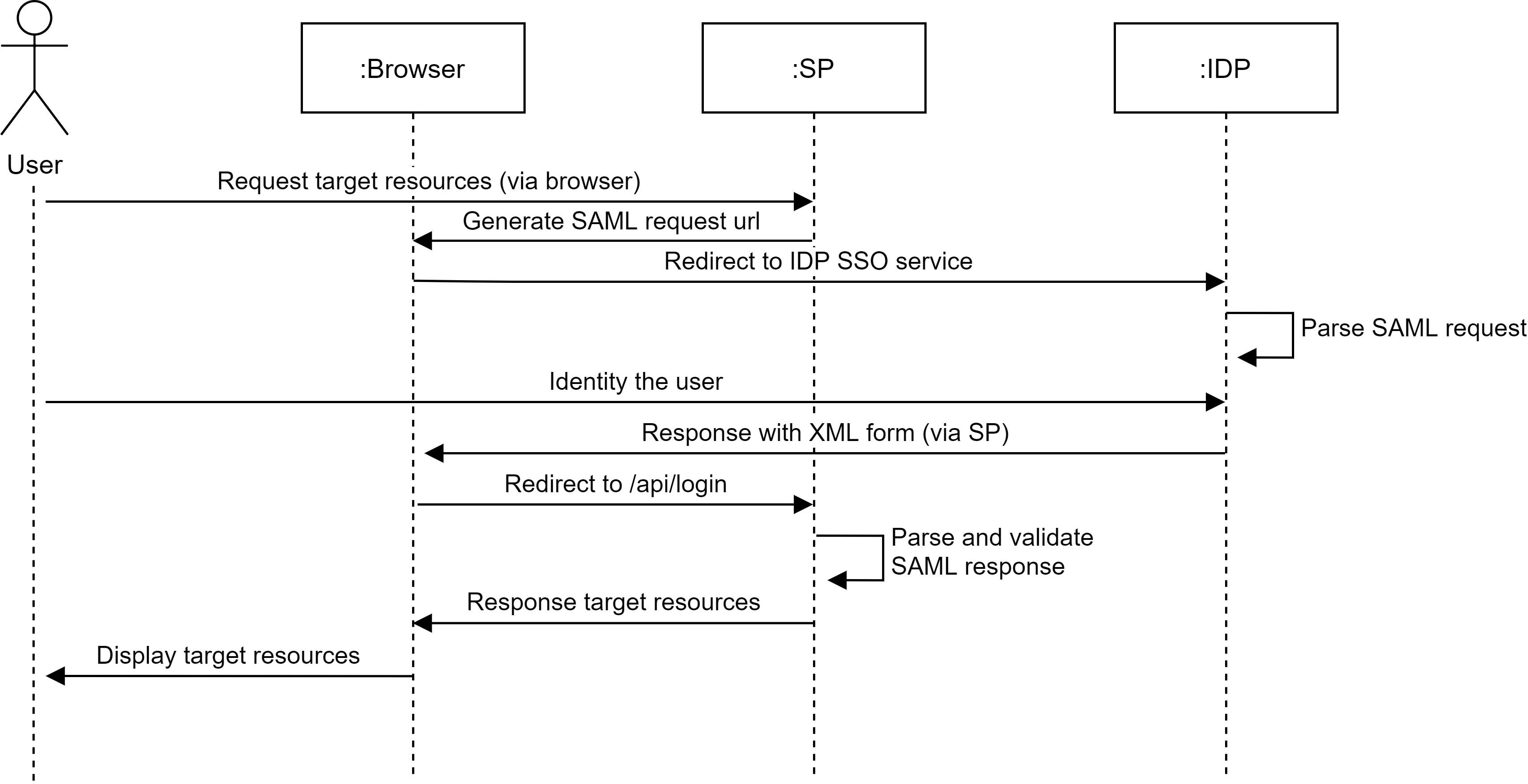
How SAML integration works
When using SAML SSO, users log into Casdoor via the identity provider without ever passing credentials to Casdoor. The progress is shown in the following diagram.